|
Poslao: 08 Feb 2010 22:57
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
Svakog drugog utorka u mesecu Microsoft objavljuje zakrpe za svoj softver - ovaj put je u pitanju trinaest update-a.
Pet kritičnih, sedam važnih i jedan umereno važan.
Jedanaest zakrpi je za različite verzije Windowsa, dok su preostale dve za Office XP / 2003 (Win) i Office 2004 (OS X).
Tačni detalji naravno nisu poznati (kako bi se umanjila verovatnoća zloupotrebe propusta), no pretpostavlja se da će MS izdati zakrpu za 17 godina * star bug u jezgrima svih 32-bitnih verzija Windowsa koji može biti iskorišćen za preuzimanje kontrole nad računarom.
* 
|
|
|
|
|
Registruj se da bi učestvovao u diskusiji. Registrovanim korisnicima se NE prikazuju reklame unutar poruka.
|
|
|
|
|
|
|
Poslao: 13 Dec 2011 23:51
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
MS11-087 - Critical : Vulnerability in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2639417) - Version: 1.0
Severity Rating: Critical
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted document or visits a malicious Web page that embeds TrueType font files.
MS11-088 - Important : Vulnerability in Microsoft Office IME (Chinese) Could Allow Elevation of Privilege (2652016) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Office IME (Chinese). The vulnerability could allow elevation of privilege if a logged-on user performed specific actions on a system where an affected version of the Microsoft Pinyin (MSPY) Input Method Editor (IME) for Simplified Chinese is installed. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full administrative rights. Only implementations of Microsoft Pinyin IME 2010 are affected by this vulnerability. Other versions of Simplified Chinese IME and other implementations of IME are not affected.
MS11-089 - Important : Vulnerability in Microsoft Office Could Allow Remote Code Execution (2590602) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Word file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS11-090 - Critical : Cumulative Security Update of ActiveX Kill Bits (2618451) - Version: 1.0
Severity Rating: Critical
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft software. The vulnerability could allow remote code execution if a user views a specially crafted Web page that instantiates a specific ActiveX control with Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. This update also includes kill bits for four third-party ActiveX controls.
MS11-091 - Important : Vulnerabilities in Microsoft Publisher Could Allow Remote Code Execution (2607702) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves four privately reported vulnerabilities in Microsoft Office. The most severe vulnerabilities could allow remote code execution if a user opens a specially crafted Publisher file. An attacker who successfully exploited any of these vulnerabilities could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS11-092 - Critical : Vulnerability in Windows Media Could Allow Remote Code Execution (2648048-) - Version: 1.0
Severity Rating: Critical
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Windows Media Player and Windows Media Center. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Digital Video Recording (.dvr-ms) file. In all cases, a user cannot be forced to open the file; for an attack to be successful, a user must be convinced to do so.
MS11-093 - Important : Vulnerability in OLE Could Allow Remote Code Execution (2624667) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in all supported editions of Windows XP and Windows Server 2003. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability. For more information, see the subsection, Affected and Non-Affected Software, in this section. The vulnerability could allow remote code execution if a user opens a file that contains a specially crafted OLE object. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS11-094 - Important : Vulnerabilities in Microsoft PowerPoint Could Allow Remote Code Execution (2639142) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves two privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted PowerPoint file. An attacker who successfully exploited either of the vulnerabilities could take complete control of an affected system. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
MS11-095 - Important : Vulnerability in Active Directory Could Allow Remote Code Execution (2640045) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Active Directory, Active Directory Application Mode (ADAM), and Active Directory Lightweight Directory Service (AD LDS). The vulnerability could allow remote code execution if an attacker logs on to an Active Directory domain and runs a specially crafted application. To exploit this vulnerability, an attacker would first need to acquire credentials to log on to an Active Directory domain.
MS11-096 - Important : Vulnerability in Microsoft Excel Could Allow Remote Code Execution (2640241) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Excel file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Installing and configuring Office File Validation (OFV) to prevent the opening of suspicious files blocks the attack vectors for exploiting the vulnerabilities described in CVE-2011-3403.
MS11-097 - Important : Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege (2620712) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application designed to send a device event message to a higher-integrity process. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
MS11-098 - Important : Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2633171) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application designed to exploit the vulnerability. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
MS11-099 - Important : Cumulative Security Update for Internet Explorer (2618444) - Version: 1.0
Severity Rating: Important
Revision Note: V1.0 (December 13, 2011): Bulletin published.
Summary: This security update resolves three privately reported vulnerabilities in Internet Explorer. The most severe vulnerability could allow remote code execution if a user opens a legitimate HyperText Markup Language (HTML) file that is located in the same directory as a specially crafted dynamic link library (DLL) file.
Malicious Software Removal Tool:
32 bit: [Link mogu videti samo ulogovani korisnici]
64 bit: [Link mogu videti samo ulogovani korisnici]
|
|
|
|
|
|
|
Poslao: 14 Dec 2011 16:49
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
ISO slika bezbednosnog izdanja, decembar 2011. (Security Release ISO Image December 2011)
Citat:Ova DVD5 ISO datoteka slike sadrži bezbednosne ispravke za Windows objavljene na lokaciji Windows Update 13. decembra 2011. Slika ne sadrži bezbednosne ispravke za druge Microsoft proizvode. Ova DVD5 ISO slika namenjena je za administratore korporacija koji preuzimaju više individualnih jezičkih verzija za svaku bezbednosnu ispravku i koji ne koriste automatizovano rešenje poput Windows Server Update Services (WSUS). Možete koristiti ovu ISO sliku da biste preuzeli više ispravki na svim jezicima odjednom.
[Link mogu videti samo ulogovani korisnici]
|
|
|
|
|
|
|
Poslao: 07 Jan 2012 18:59
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
Januarski patch tuesday će biti neobično "bogat"... 
This month’s release includes seven bulletins addressing eight vulnerabilities in Microsoft Windows and Microsoft Developer Tools And Software.
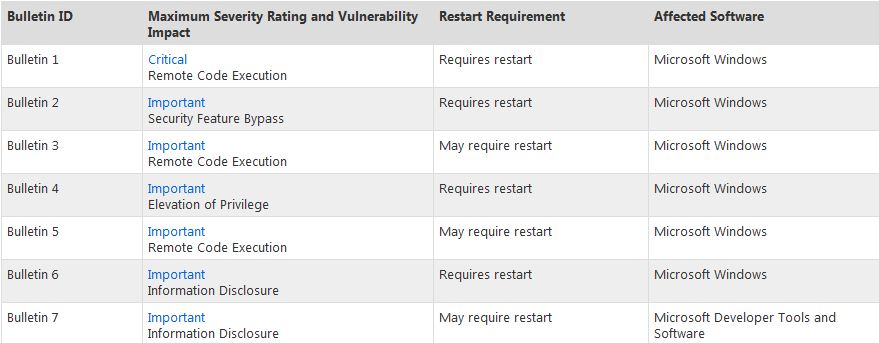
Critical Security Bulletins
============================
Bulletin 1
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation not affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation not affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and
Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and
Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and
Windows Server 2008 R2 for x64-based Systems Service Pack 1
(Windows Server 2008 R2 Server Core installation affected)
- Windows Server 2008 R2 for Itanium-based Systems and
Windows Server 2008 R2 for Itanium-based Systems
Service Pack 1
- Impact: Elevation of Privilege
Citat:In addition, eagle-eyed readers of the summary page will notice an unusual vulnerability classification, “Security Feature Bypass,” for one of our Important-severity bulletins. SFB-class issues in themselves can’t be leveraged by an attacker; rather, a would-be attacker would use them to facilitate use of another exploit.
Source: TechNet.
Citat:Andrew Storms, director of security operations at nCircle Security, took a shot at deciphering the new category.
"Someone probably discovered a method to either turn off or bypass one of Windows security features that could let an attacker get in easier," said Storms, who said the possibilities of the vulnerable element could range from UAC -- for "user account control," the prompt users must click through to install software, to DEP and ASLR, two important anti-exploit technologies baked into Windows.
In an email, Paul Harvey, a security and forensic analyst with Lumension, flatly said that the security bypass feature (dubbed "SBF" by Microsoft) patch would "update ... Microsoft's SEHOP technology to enhance the defense-in-depth capability that it can afford to legacy applications."
SEHOP, or Structured Exception Handler Overwrite Protection, is a label for an anti-exploit technology that designed to block a now-common hacking technique first described in 2003, according to a Microsoft Security Research & Defense blog post from 2009.
Microsoft added SEHOP defenses to Windows with Vista Service Pack 1 (SP1); it's also inside Windows 7, Server 2008 and Server 2008 R2, although it's disabled by default on Vista and Windows 7, Microsoft says, "for compatibility reasons."
It's possible that Microsoft will enable SEHOP by default in those client editions of Windows with next Tuesday's patch.
Citat:Microsoft declined to say whether next week's update tally will include a fix for a long-standing issue in SSL (secure socket layer) 3.0 and TLS (transport layer security) 1.0 within Windows that was publicized last September by a pair of researchers who built BEAST, or "Browser Exploit Against SSL/TLS," a hacking tool and the first-ever practical exploit of the years-old flaw.
Although a patch for the bug exploited by BEAST was scheduled to ship in December 2011, Microsoft scratched the release at the last moment because German enterprise developer SAP reported compatibility problems.
"Microsoft continues to work with SAP and will release the update through our normal bulletin process," said Dave Forstrom, director of Microsoft's Trustworthy Computing group, today when asked if a BEAST patch was on the docket for next Tuesday.
"It's gonna be in there," said Storms of Microsoft's fix. "It's my understanding that the SAP patch is already out."
Source: [Link mogu videti samo ulogovani korisnici]
|
|
|
|
|
|
|
|
|
Poslao: 08 Jan 2012 18:43
|
offline
- Sass Drake

- Anti Malware Fighter
Rank 2


- Pridružio: 26 Avg 2010
- Poruke: 10622
- Gde živiš: Hypnos Control Room, Tokyo Metropolitan Government Building
|
Citat:Critical Security Bulletins
============================
Bulletin 1
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and
Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and
Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and
Windows Server 2008 R2 for x64-based Systems Service Pack 1
(Windows Server 2008 R2 Server Core installation not affected)
- Windows Server 2008 R2 for Itanium-based Systems and
Windows Server 2008 R2 for Itanium-based Systems
Service Pack 1
- Impact: Remote Code Execution
- Version Number: 1.0
Important Security Bulletins
============================
Bulletin 2
- Affected Software:
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and
Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and
Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and
Windows Server 2008 R2 for x64-based Systems Service Pack 1
(Windows Server 2008 R2 Server Core installation affected)
- Windows Server 2008 R2 for Itanium-based Systems and
Windows Server 2008 R2 for Itanium-based Systems
Service Pack 1
- Impact: Security Feature Bypass
- Version Number: 1.0
Bulletin 3
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Impact: Remote Code Execution
- Version Number: 1.0
Bulletin 4
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Impact: Elevation of Privilege
- Version Number: 1.0
Bulletin 5
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation not affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation not affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and
Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and
Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and
Windows Server 2008 R2 for x64-based Systems Service Pack 1
(Windows Server 2008 R2 Server Core installation not affected)
- Windows Server 2008 R2 for Itanium-based Systems and
Windows Server 2008 R2 for Itanium-based Systems
Service Pack 1
- Impact: Remote Code Execution
- Version Number: 1.0
Bulletin 6
- Affected Software:
- Windows XP Service Pack 3
- Windows XP Professional x64 Edition Service Pack 2
- Windows XP Professional x64 Edition Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 x64 Edition Service Pack 2
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Server 2003 with SP2 for Itanium-based Systems
- Windows Vista Service Pack 2
- Windows Vista x64 Edition Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for x64-based Systems Service Pack 2
(Windows Server 2008 Server Core installation affected)
- Windows Server 2008 for Itanium-based Systems Service Pack 2
- Windows 7 for 32-bit Systems and
Windows 7 for 32-bit Systems Service Pack 1
- Windows 7 for x64-based Systems and
Windows 7 for x64-based Systems Service Pack 1
- Windows Server 2008 R2 for x64-based Systems and
Windows Server 2008 R2 for x64-based Systems Service Pack 1
(Windows Server 2008 R2 Server Core installation affected)
- Windows Server 2008 R2 for Itanium-based Systems and
Windows Server 2008 R2 for Itanium-based Systems
Service Pack 1
- Impact: Information Disclosure
- Version Number: 1.0
Bulletin 7
- Affected Software:
- Microsoft Developer Tools and Software
- Impact: Information Disclosure
- Version Number: 1.0
|
|
|
|
|
|
|
Poslao: 10 Jan 2012 20:51
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
Microsoft Security Bulletin MS12-001 - Important
Vulnerability in Windows Kernel Could Allow Security Feature Bypass (2644615)
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow an attacker to bypass the SafeSEH security feature in a software application. An attacker could then use other vulnerabilities to leverage the structured exception handler to run arbitrary code. Only software applications that were compiled using Microsoft Visual C++ .NET 2003 can be used to exploit this vulnerability.
More information on the impact of MS12-001: [Link mogu videti samo ulogovani korisnici]
Microsoft Security Bulletin MS12-002 - Important
Vulnerability in Windows Object Packager Could Allow Remote Code Execution (2603381)
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a legitimate file with an embedded packaged object that is located in the same network directory as a specially crafted executable file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Microsoft Security Bulletin MS12-003 - Important
Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege (2646524)
This security update resolves one privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application. The attacker could then take complete control of the affected system and install programs; view, change, or delete data; or create new accounts with full user rights. This vulnerability can only be exploited on systems configured with a Chinese, Japanese, or Korean system locale
Microsoft Security Bulletin MS12-004 - Critical
Vulnerabilities in Windows Media Could Allow Remote Code Execution (2636391)
This security update resolves two privately reported vulnerabilities in Microsoft Windows. The vulnerabilities could allow remote code execution if a user opens a specially crafted media file. An attacker who successfully exploited the vulnerabilities could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Microsoft Security Bulletin MS12-005 - Important
Vulnerability in Microsoft Windows Could Allow Remote Code Execution (2584146)
This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Office file containing a malicious embedded ClickOnce application. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
Microsoft Security Bulletin MS12-006 - Important
Vulnerability in SSL/TLS Could Allow Information Disclosure (2643584)
This security update resolves a publicly disclosed vulnerability in SSL 3.0 and TLS 1.0. This vulnerability affects the protocol itself and is not specific to the Windows operating system. The vulnerability could allow information disclosure if an attacker intercepts encrypted web traffic served from an affected system. TLS 1.1, TLS 1.2, and all cipher suites that do not use CBC mode are not affected.
Microsoft Security Bulletin MS12-007 - Important
Vulnerability in AntiXSS Library Could Allow Information Disclosure (2607664)
This security update resolves one privately reported vulnerability in the Microsoft Anti-Cross Site Scripting (AntiXSS) Library. The vulnerability could allow information disclosure if an attacker passes a malicious script to a website using the sanitization function of the AntiXSS Library. The consequences of the disclosure of that information depends on the nature of the information itself. Note that this vulnerability would not allow an attacker to execute code or to elevate the attacker's user rights directly, but it could be used to produce information that could be used to try to further compromise the affected system. Only sites that use the sanitization module of the AntiXSS Library are affected by this vulnerability.
|
|
|
|
|
|
|
Poslao: 10 Jan 2012 21:00
|
offline
- dr_Bora

- Anti Malware Fighter
Rank 2


- Pridružio: 24 Jul 2007
- Poruke: 12280
- Gde živiš: Höganäs, SE
|
Malicious Software Removal Tool:
32 bit: [Link mogu videti samo ulogovani korisnici]
64 bit: [Link mogu videti samo ulogovani korisnici]
|
|
|
|
|
|

